【以下記事は自動翻訳です】
世界中で、静かだが意図的なサイバー侵入の波が押し寄せている。これらは騒がしいランサムウェア攻撃や無秩序なデータ漏洩ではない。長期的な持続を目的とした計算された工作だ。背後にいる攻撃者は、通信事業者、ルーター、電力網、政府インフラといった日常生活を支えるシステムを戦略的に移動し、ほとんど痕跡を残さない。
これらの脅威グループは総称して「タイフーン」と呼ばれ、Volt Typhoon、フラックス・タイフーン、Salt Typhoonが含まれ、いずれも中国国家が支援する活動と関連している。各グループは異なる目的で活動するが、その手法には共通のDNAが存在する:ステルス性、忍耐力、そして深い作戦理解である。カスタムマルウェアを展開する代わりに マルウェアではなく、信頼されたツールを流用し、正当なシステム活動に溶け込む手法を用いる。
破壊活動のための事前配置から秘密通信諜報活動に至るまで、タイフーンは、気づかれないからこそ成功する攻撃への転換を体現している。
台風名簿
各タイフーングループは、世界的な重要インフラを標的とする広範な戦略において役割を担っている。任務は異なるものの、その手法は一貫して不可視性と持続性を最優先する。
道具なしの戦術:Living Off the Land
タイフーン作戦の検知 困難な理由は、彼らの技術力だけでなく抑制力検知 。彼らは新たなコードをほとんど展開せず、代わりに環境内に既に存在するものを活用する。
この 「現地資源活用型」 という手法は、PowerShell、WMIC、netsh、リモートデスクトップといった正当な管理ツールを悪用し、通常の操作を装って悪意のある活動を実行する。これらのツールは企業環境で広く使用されているため、異常な動作はノイズの中に埋もれやすく、検知が困難となる。
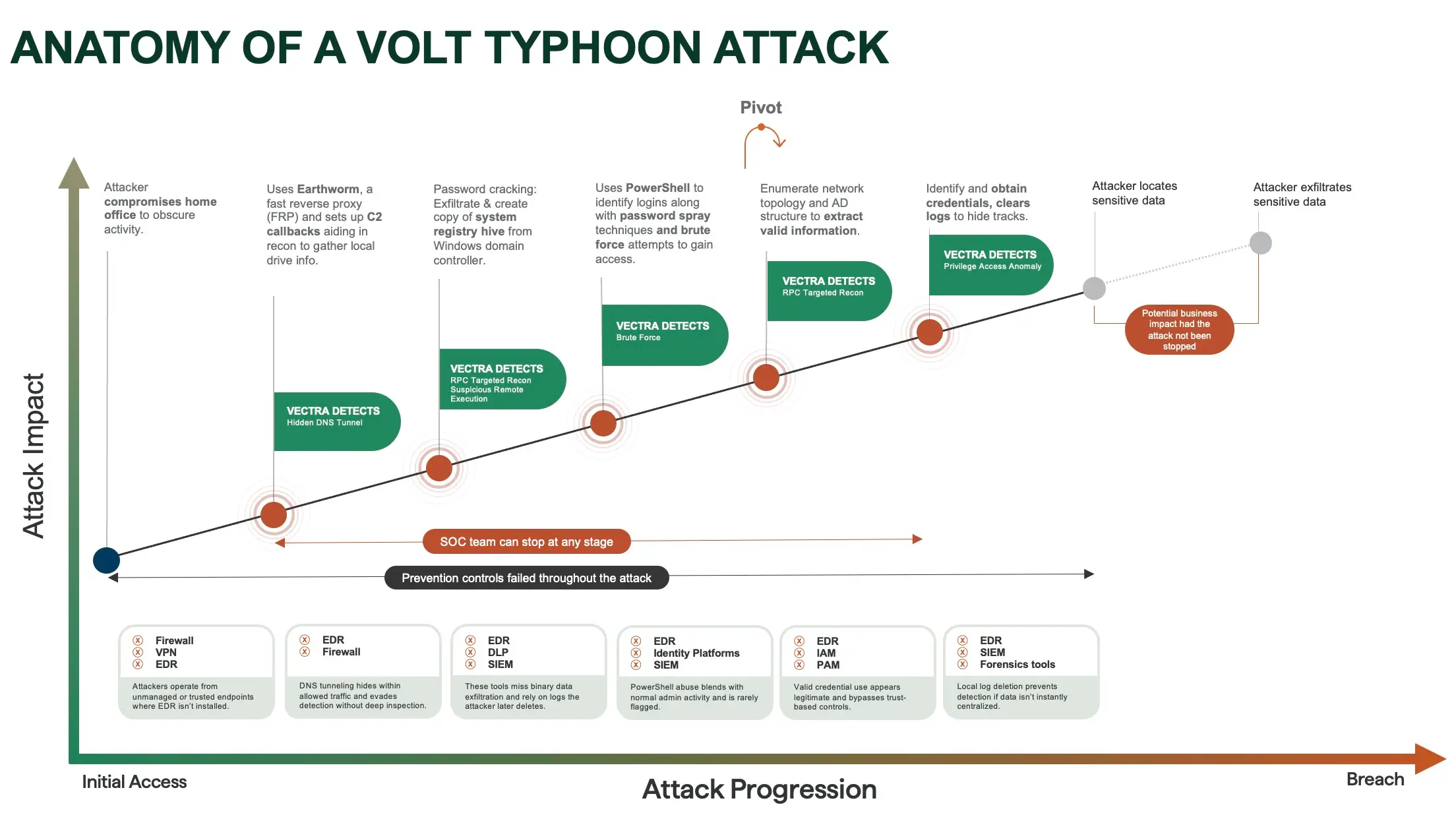
Volt Typhoon この戦術を多用して密かに情報を収集したり、長期的な足場を築いたりしている。Salt Typhoon は、カーネルレベルインプラントなどの高度なステルス技術とネイティブツールを組み合わせて、より深いアクセスを維持する。統一された目標:任務を遂行しつつ、ごく普通の存在であるように見せかけること。
ペイロードに対する持続性
台風グループにとって、侵入は第一段階に過ぎない。真の目的は、可能な限り長く標的内部に潜伏し、発見を避けつつ永続的なアクセス経路を構築することだ。これは従来のペイロードを届けることではない。環境を形作り、決して去らなくて済むようにすることである。
フラックス・タイフーン 正当なVPNクライアント(例:SoftEther)をインストールすることでリモートアクセスを維持し、通常のトラフィックパターンに溶け込ませる。場合によっては、Windowsのアクセシビリティ機能(例:スティッキーキーのショートカット)を乗っ取り、再起動後も存続しエンドポイント監視を回避するログインバックドアを密かに作成する。
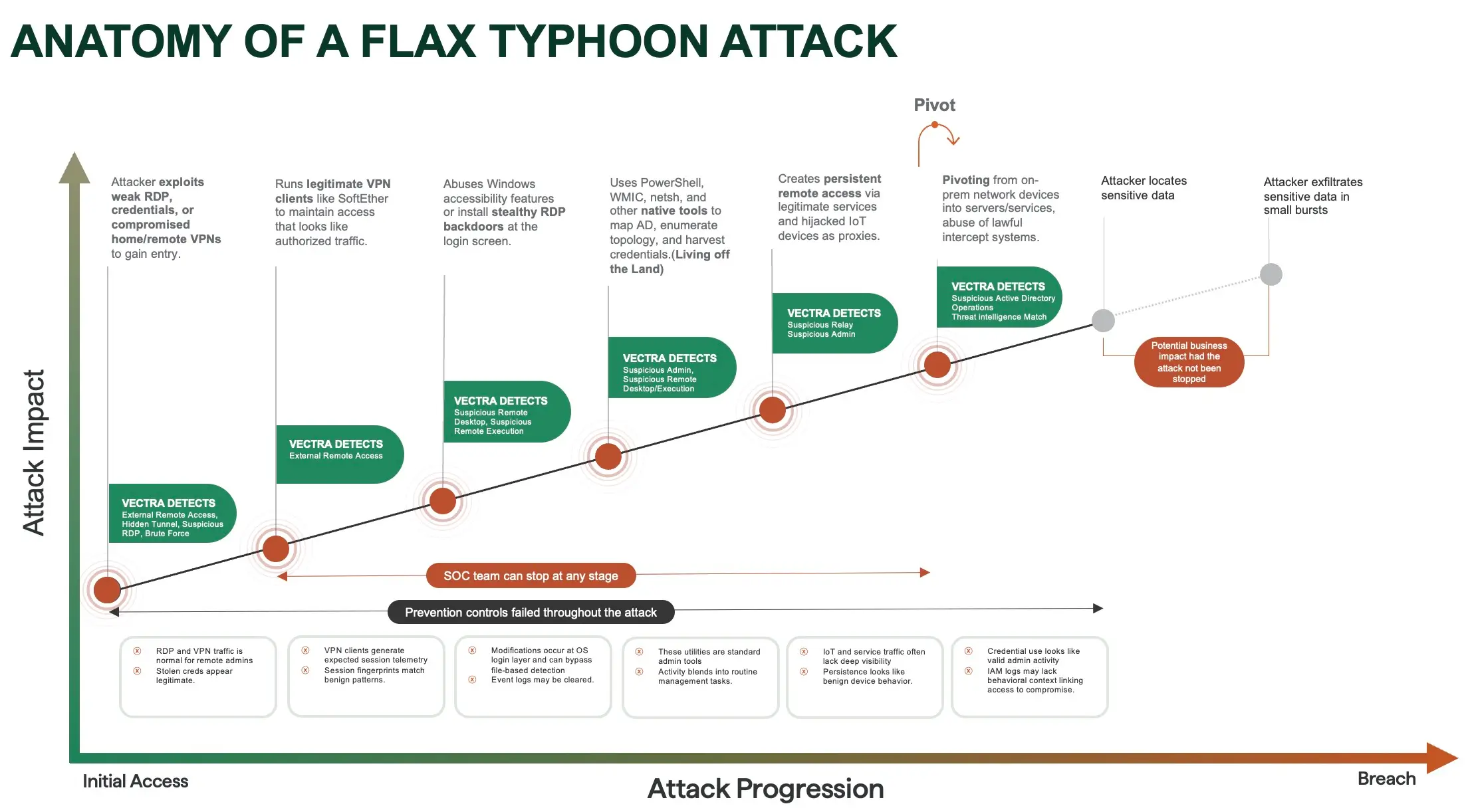
Volt Typhoon 盗まれた認証情報とネイティブのWindowsユーティリティを利用して、ネットワーク内を検知されずに移動する。netsh portproxyなどのツールを用いて隠密なトンネルを構築することが多く、これによりアラートを発生させずに内部トラフィックをリダイレクトでき、外部コマンド&コントロールインフラに依存する必要もない。
Salt Typhoon ステルス性と高度な技術的制御を組み合わせる。アクセスを維持するためにルーターやネットワーク機器を悪用するだけでなく、カーネルレベルで動作するルートキットを展開する。休眠状態のサービスを有効化し、アクセス制御を変更し、デバイス設定を操作してネットワークへの複数の永続的な経路を確保する様子が確認されている。
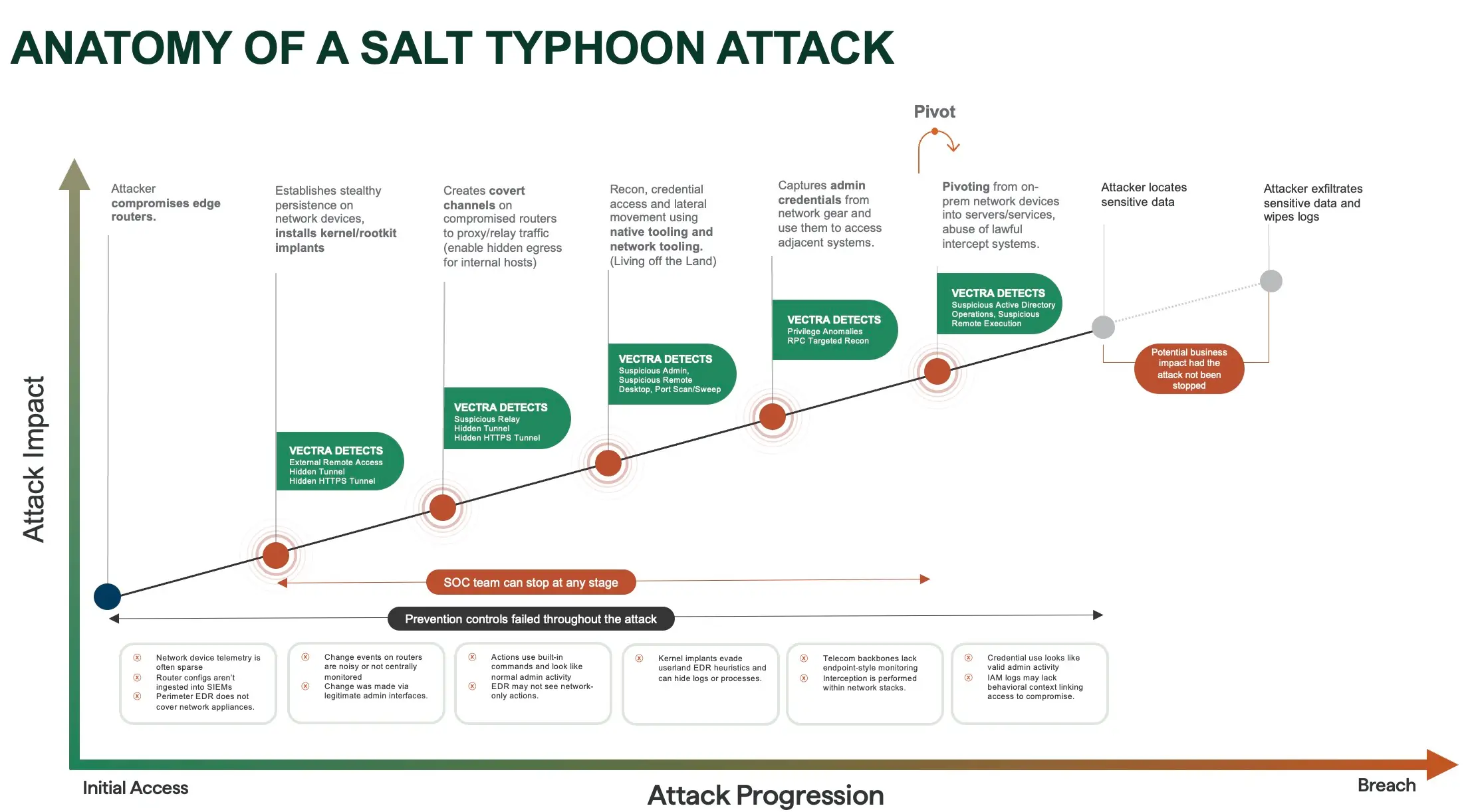
これらの攻撃者はネットワーク内に潜むだけでなく、自らを中心にネットワークを再構築します。その持続的活動モデルにより、防御側は単なる検索ではなく、時間軸に沿った行動の監視を余儀なくされる。 マルウェアシグネチャを探すのではなく、時間をかけて振る舞いを監視することを防御側に強いる。
持続こそがペイロードである
Volt Typhoonが妨害の準備を進めているにせよ、Flax Typhoonが台湾のインフラをマッピングしているにせよ、Salt Typhoonが世界中のバックボーンの通信を傍受しているにせよ、共通点は明らかです。マルウェアはもはや侵害の指標ではなく、振る舞いが指標なのです。これらのグループはいずれも階層化されたアクセスを構築し、信頼関係を操作し、従来の検出の閾値をはるかに下回る活動を行っています。防御側が振る舞いではなくファイルに重点を置くことを期待しているのです。
ここで Vectra AIプラットフォームが重要な差別化を実現します。クラウド、ネットワーク、アイデンティティを横断した行動を分析することで、Vectra Typhoon攻撃者が依存するコマンド使用、権限昇格、ラテラルムーブの微妙なパターンをVectra 。このプラットフォームはmalwareを探すのではなく、攻撃者が正当に見えても悪意のある意図を特定します。
検知戦略が明らかな脅威のみに焦点を当てている場合、攻撃者は成功します。発見を望まない脅威を暴くには、攻撃者の適応に合わせて学習するAI主導 と、継続的な可視性 が必要です。

