なぜ EDR と NDR の併用が不可欠なのか
攻撃者は一か所にとどまりません。エンドポイント、ID、クラウドサービス、ネットワークパスを横断的に移動し、価値を引き出し、業務を妨害します。単一の制御ではこの動きを追い切れないため、効果的な防御には EDR と NDR が連携して機能することが必要です。
エンドポイントは、何が実行され、攻撃者がどのようにデバイスを操作したか を示します。
ネットワークは、攻撃者がどこへ移動し、どこと通信し、次に何を探ったか を示します。
これらを組み合わせることで、完全な攻撃経路が可視化され、チームは確信を持って対応できるコンテキストを得られます。
Vectra AI は CrowdStrike との統合により、エンドポイントの詳細とネットワークの洞察を結び付け、攻撃をより早く把握し、より迅速に阻止できるようにします。
調査におけるアナリストの思考プロセス
アナリストがアラートを受信すると、通常は次のような質問から調査を始めます。
- どのシステムから発生しているのか?
- 何がそれを引き起こしたのか?
- これは現実か、それとも雑音か?
- 今、それを封じ込める必要があるのか?
- 全体像は把握できているのか?
Vectra AI と CrowdStrike の統合は、これらの疑問に対する答えを提供します。
Vectra AI が CrowdStrike と統合し、脅威対応のための統合されたエンドポイント/ネットワークの洞察を提供する方法
- コンテキスト化:そのシステムが何者かを理解する

アナリストの質問:この検知はどのシステムから来ており、そのシステムについて何が分かっているのか?
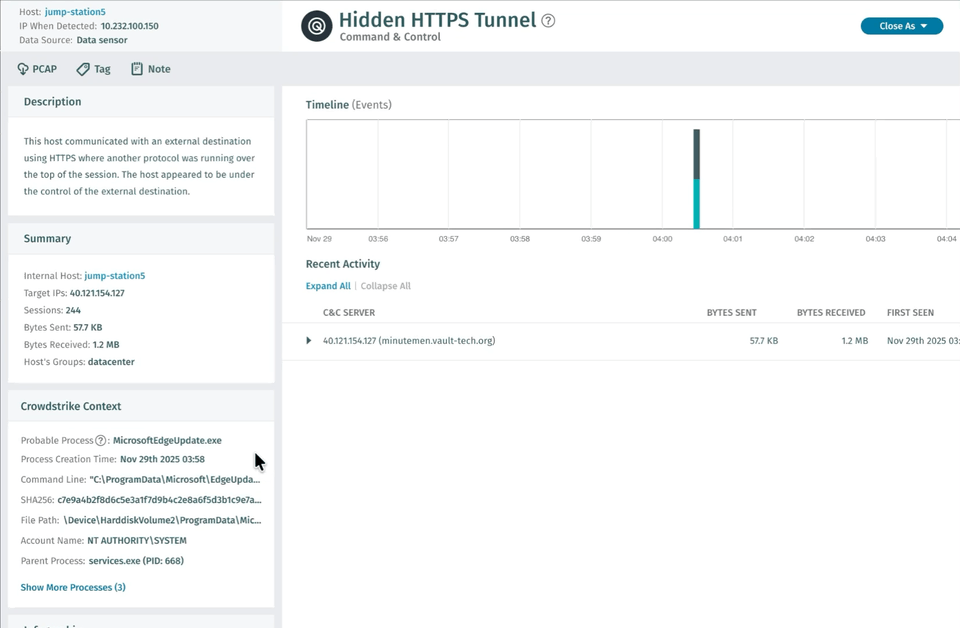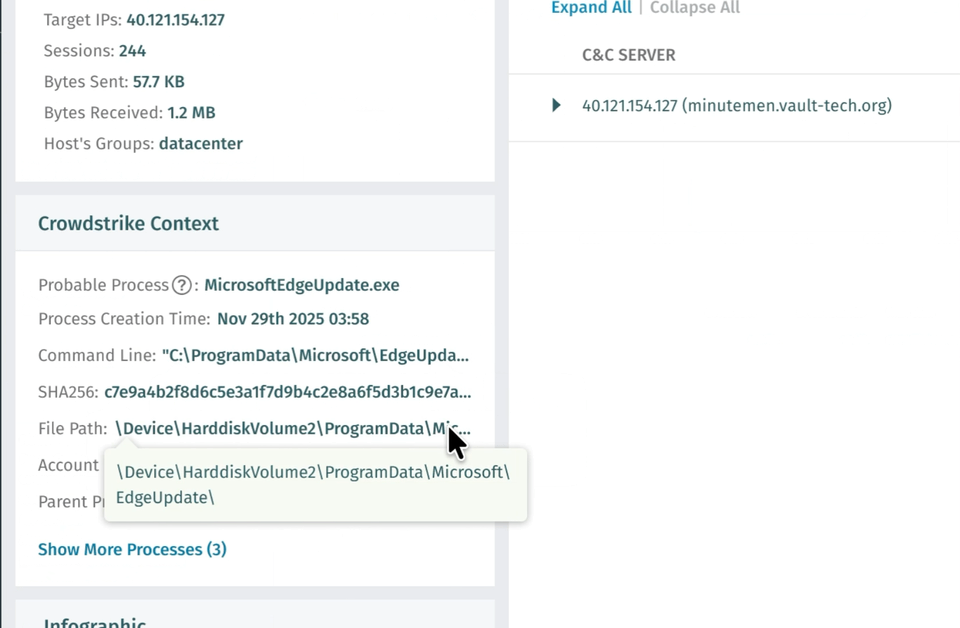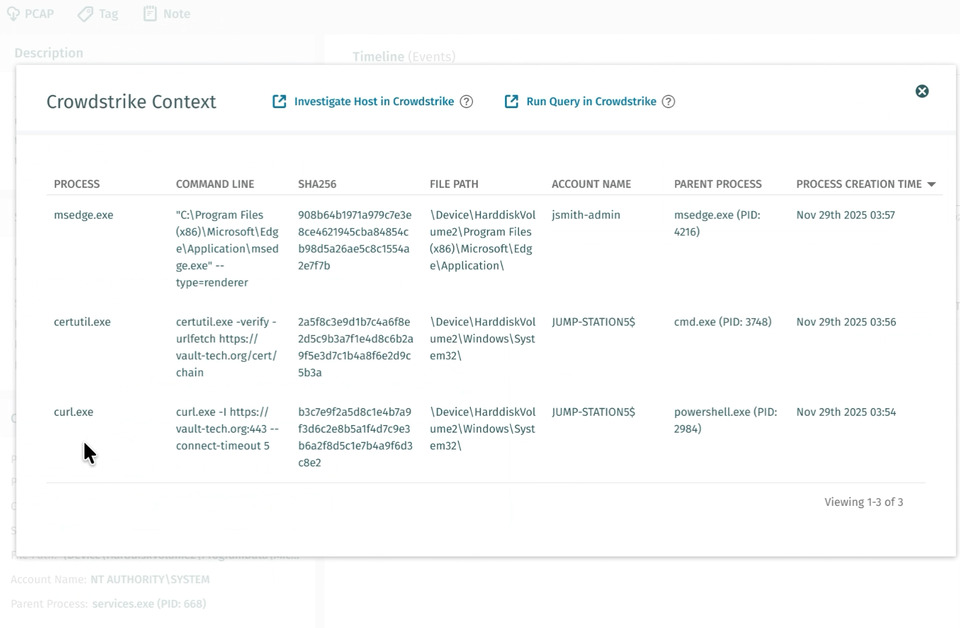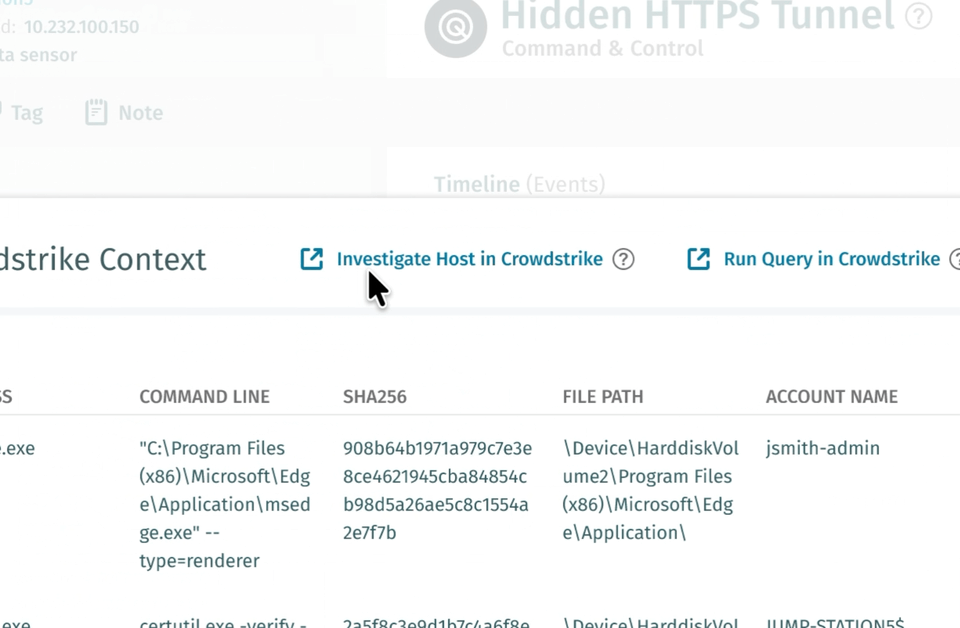
CrowdStrike EDR が稼働しているシステムは、Vectra AI プラットフォーム 内で自動的に認識されます。これにより、Vectra AI がネットワークアクティビティを正確に関連付けるための追加のホストコンテキストが提供されます。アナリストは、OS、センサー ID、最終検知時刻などの詳細を即座に確認できます。
このコンテキストにより、観測された振る舞いがそのシステムの役割に合致しているか、さらなる調査が必要かどうかを容易に判断できます。
- EDR プロセス相関:挙動を引き起こした原因を特定する
アナリストの質問:この不審なネットワーク挙動を引き起こしたプロセスは何か?
この問いは、ツールの切り替え、CrowdStrike での検索、タイムスタンプの突き合わせが必要になるため、調査を遅らせがちです。
Vectra AI の EDR Process Correlation は、この負担を取り除きます。Vectra AI が不審なネットワーク挙動を検知すると、CrowdStrike に対して自動的に問い合わせを行い、該当するプロセスと検知を相関付けます。アナリストは、ファイル名、コマンドライン、ハッシュ、実行時刻、親プロセスといった情報を、Vectra AI の画面内ですぐに確認できます。
これにより、手動ワークフローは自動化されます。カスタム SIEM や SOAR の相関ロジックは不要となり、1 件の検知あたり最大 30 分の時間を節約できます。さらに詳細な分析が必要な場合は、事前に入力された CrowdStrike へのリンクから、該当するプロセスツリーを直接開くことができます。
- 即時の封じ込め:ツールを切り替えずに対応する

アナリストの質問:このシステムを今すぐ封じ込める必要があるか? それをここから実行できるか?
脅威が確認された場合、1 秒 1 秒が重要です。Vectra AI の 360 Response は CrowdStrike と統合されており、自動または手動で、Vectra AI プラットフォーム から直接ホスト封じ込めを実行できます。
不審なネットワーク挙動が、そのまま CrowdStrike によるホストロックダウンを自動的にトリガーできます。アナリストはツールを切り替えたり、複数ステップの対応フローを辿ったりする必要がありません。アーキテクトにとっても、脆弱なカスタムロジックに依存しない、より信頼性が高く保守しやすい対応フローが実現します。
- CrowdStrikeの次世代SIEMとの統合
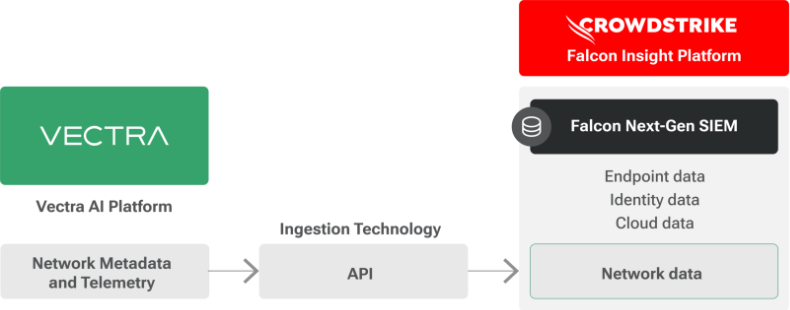
アナリストの質問:このアクティビティを SIEM で検証できるか?
Vectra AI は、ネットワークメタデータおよび AI により強化されたテレメトリを、Falcon 取り込み API を通じて CrowdStrike Falcon Next-Gen SIEM に直接ストリーミングします。Falcon Next-Gen SIEM は、エンドポイント、ID、クラウド、ネットワークにまたがるペタバイト級のデータを分析でき、Vectra AI はその統合データセットに対して、クラス最高のネットワーク可視性を提供します。アナリストは、Vectra AI の検知から Falcon Next-Gen SIEM にワンクリックでピボットし、高速なクエリエンジンと可視化機能を使って、より深い調査を行うことができます。
Vectra AI の検知と、それを支えるネットワーク挙動を CrowdStrike のリアルタイム SIEM パイプラインに提供することで、SOC チームは複数のログシステムや相関ワークフローを管理することなく、エンドポイントとネットワーク全体にわたる脅威を一元的に把握できます。
- エンドポイントとネットワークを横断した統合シグナルVectraVectra MCPサーバーによる実現
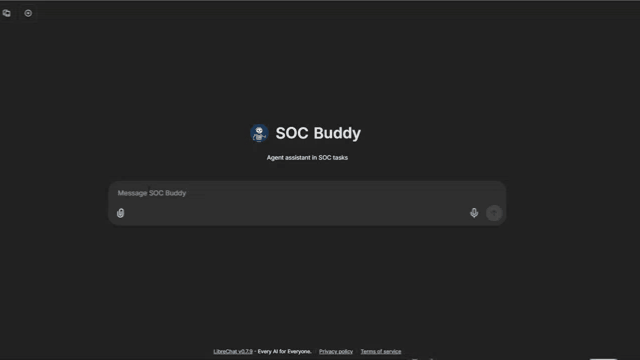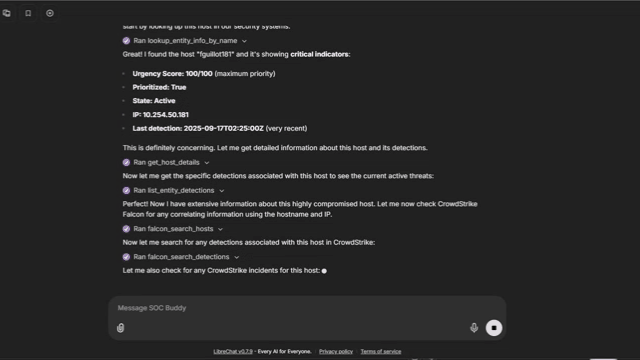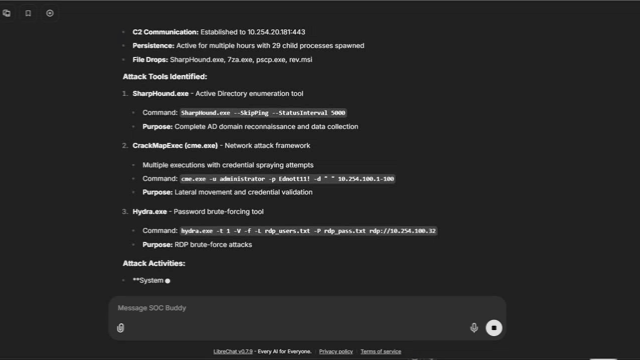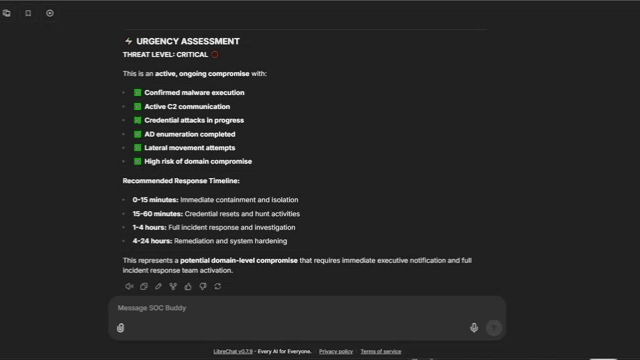
アナリストの質問:このアラートに関するエンドポイントおよびネットワークのコンテキストを、1 か所ですべて取得できるか?
Vectra AI MCP Server は、NDR と EDR の両方からのシグナルを、構造化されたインメモリのコンテキストレイヤーに統合する、共有の演算およびコンテキストエンジンとして機能します。システム間の往復を排除し、参照遅延を低減することで、MCP は調査のあらゆるステップを高速化し、MTTR を短縮します。アナリストや自動化エージェントは、必要な完全なコンテキストを 1 か所で取得できるため、脅威の検証と対応を大幅に迅速かつ正確に行えます。
実際のシグナルの明確さ
これらの機能により、Vectra AI と CrowdStrike は、ドメインを横断した攻撃を統合・自動化された形で可視化し、チームが「何が起き、どこで対処すべきか」を迅速に理解するために必要なシグナルの明確さを提供します。
攻撃者が従来型の制御を回避するために、エンドポイント技術とネットワーク移動を組み合わせるケースが増える中、EDR と NDR のテレメトリを統合することで、初動プロセスとその完全なネットワークフットプリントの両方が可視化され、調査開始時点から完全なクロスドメインの状況把握が可能になります。
ツール間の手動ピボットを必要とする代わりに、Vectra AI は資産を自動的に特定し、関連するプロセス情報を取得し、適切な対応をリアルタイムでトリガーします。これにより、アナリストはデータ収集に費やす時間を減らし、本当に重要な攻撃の阻止に集中できます。
実際の動作を見る
Vectra AI がどのようにエンドポイントのプロセスコンテキストをネットワーク検知と自動的に結び付け、CrowdStrike を通じてワンクリックでホスト隔離を実現するのかをご覧ください。
デモはこちらです。

